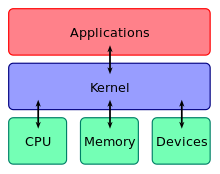
An operating system (OS) is system software that manages computer hardware and software resources and provides common services for computer programs.
The operating system is an essential component of the system software in a computer system.
Application programs usually require an operating system to function.
Time-sharing operating systems schedule tasks for efficient use of the system and may also include accounting software for cost allocation of processor time, mass storage, printing, and other resources.
For hardware functions such as input and output and memory allocation, the operating system acts as an intermediary between programs and the computer hardware, although the application code is usually executed directly by the hardware and frequently makes system calls to an OS function or be interrupted by it.
Operating systems are found on many devices that contain a computer—from cellular phones and video game consoles to web servers and supercomputers.
Examples of popular modern operating systems include Android, BlackBerry, BSD, Chrome OS, iOS, Linux, OS X, QNX, Steam OS, Microsoft Windows (and variant Windows Phone), and z/OS. The first nine of these examples share roots in Unix. Popular hard real-time operating systems include FreeRTOS, Micrium and VxWorks.
TYPES OF OPERATING SYSTEMS
1. Single- and multi-tasking
- A single-tasking system can only run one program at a time, while a multi-tasking operating system allows more than one program to be running in concurrency.
- This is achieved by time-sharing, dividing the available processor time between multiple processes which are each interrupted repeatedly in time-slices by a task scheduling subsystem of the operating system.
- Multi-tasking may be characterized in pre-emptive and co-operative types.
- In pre-emptive multitasking, the operating system slices the CPU time and dedicates a slot to each of the programs.
- EXAMPLE - Unix, Solaris, Linux, AmigaOS support pre-emptive multitasking.
- Cooperative multitasking is achieved by relying on each process to provide time to the other processes in a defined manner.
- 16-bit versions of Microsoft Windows used cooperative multi-tasking. 32-bit versions of both Windows NT and Win9x, used pre-emptive multi-tasking.
2. Single- and multi-user
- Single-user operating systems have no facilities to distinguish users, but may allow multiple programs to run in tandem.
- A multi-user operating system extends the basic concept of multi-tasking with facilities that identify processes and resources, such as disk space, belonging to multiple users, and the system permits multiple users to interact with the system at the same time.
- Time-sharing operating systems schedule tasks for efficient use of the system and may also include accounting software for cost allocation of processor time, mass storage, printing, and other resources to multiple users.
3. Distributed
- A distributed operating system manages a group of distinct computers and makes them appear to be a single computer.
- The development of networked computers that could be linked and communicate with each other gave rise to distributed computing.
- Distributed computations are carried out on more than one machine. When computers in a group work in cooperation, they form a distributed system.
4. Templated
- In an OS, distributed and cloud computing context, templating refers to creating a single virtual machine image as a guest operating system, then saving it as a tool for multiple running virtual machines .
- The technique is used both in virtualization and cloud computing management, and is common in large server warehouses.
5. Embedded
- Embedded operating systems are designed to be used in embedded computer systems. They are designed to operate on small machines like PDAs with less autonomy.
- They are able to operate with a limited number of resources.
- They are very compact and extremely efficient by design.
- Windows CE and Minix 3 are some examples of embedded operating systems.
6. Real-time
- A real-time operating system is an operating system that guarantees to process events or data within a certain short amount of time.
- A real-time operating system may be single- or multi-tasking, but when multitasking, it uses specialized scheduling algorithms so that a deterministic nature of behaviour is achieved.
- An event-driven system switches between tasks based on their priorities or external events while time-sharing operating systems switch tasks based on clock interrupts.
COMPONENTS OF OPERATING SYSTEM
The components of an operating system all exist in order to make the different parts of a computer work together. All user software needs to go through the operating system in order to use any of the hardware, whether it be as simple as a mouse or keyboard or as complex as an Internet component.
These components are :
1. Kernel
2. Networking
3. Security
4. User Interface
These components are :
1. Kernel
2. Networking
3. Security
4. User Interface
1. KERNEL
With the aid of the firmware and device drivers, the kernel provides the most basic level of control over all of the computer's hardware devices.
It manages memory access for programs in the RAM, it determines which programs get access to which hardware resources, it sets up or resets the CPU's operating states for optimal operation at all times, and it organizes the data for long-term non-volatile storage with file systems on such media as disks, tapes, flash memory, etc.
THE KERNEL HAS SUBDIVISIONS:
Program execution
- The operating system provides an interface between an application program and the computer hardware, so that an application program can interact with the hardware only by obeying rules and procedures programmed into the operating system.
- The operating system is also a set of services which simplify development and execution of application programs.
- Executing an application program involves the creation of a process by the operating system kernel which assigns memory space and other resources, establishes a priority for the process in multi-tasking systems, loads program binary code into memory, and initiates execution of the application program which then interacts with the user and with hardware devices.
Interrupts
- Interrupts are central to operating systems, as they provide an efficient way for the operating system to interact with and react to its environment.
- The alternative — having the operating system "watch" the various sources of input for events (polling) that require action — can be found in older systems with very small stacks (50 or 60 bytes) but is unusual in modern systems with large stacks.
- Interrupt-based programming is directly supported by most modern CPUs. Interrupts provide a computer with a way of automatically saving local register contexts, and running specific code in response to events.
- Even very basic computers support hardware interrupts, and allow the programmer to specify code which may be run when that event takes place.
Modes
- Modern CPUs support multiple modes of operation.
- CPUs with this capability use at least two modes: protected mode and supervisor mode.
- The supervisor mode is used by the operating system's kernel for low level tasks that need unrestricted access to hardware, such as controlling how memory is written and erased, and communication with devices like graphics cards.
- Protected mode, in contrast, is used for almost everything else. Applications operate within protected mode, and can only use hardware by communicating with the kernel, which controls everything in supervisor mode.
- CPUs might have other modes similar to protected mode as well, such as the virtual modes in order to emulate older processor types, such as 16-bit processors on a 32-bit one, or 32-bit processors on a 64-bit one.

Privilege rings for the x86 available in protected mode. Operating systems determine which processes run in each mode.
Memory management
- Among other things, a multiprogramming operating system kernel must be responsible for managing all system memory which is currently in use by programs.
- This ensures that a program does not interfere with memory already in use by another program. Since programs time share, each program must have independent access to memory.
- Cooperative memory management, used by many early operating systems, assumes that all programs make voluntary use of the kernel's memory manager, and do not exceed their allocated memory. This system of memory management is almost never seen any more, since programs often contain bugs which can cause them to exceed their allocated memory. If a program fails, it may cause memory used by one or more other programs to be affected or overwritten.
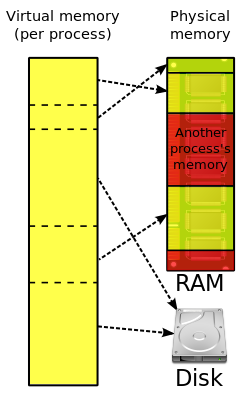
Virtual memory
- Many operating systems can "trick" programs into using memory scattered around the hard disk and RAM as if it is one continuous chunk of memory, called virtual memory.
- The use of virtual memory addressing (such as paging or segmentation) means that the kernel can choose what memory each program may use at any given time, allowing the operating system to use the same memory locations for multiple tasks.
- If a program tries to access memory that isn't in its current range of accessible memory, but nonetheless has been allocated to it, the kernel is interrupted in the same way as it would if the program were to exceed its allocated memory.
- Under UNIX this kind of interrupt is referred to as a page fault.
- When the kernel detects a page fault it generally adjusts the virtual memory range of the program which triggered it, granting it access to the memory requested. This gives the kernel discretionary power over where a particular application's memory is stored, or even whether or not it has actually been allocated yet.
- In modern operating systems, memory which is accessed less frequently can be temporarily stored on disk or other media to make that space available for use by other programs. This is called swapping, as an area of memory can be used by multiple programs, and what that memory area contains can be swapped or exchanged on demand.
- "Virtual memory" provides the programmer or the user with the perception that there is a much larger amount of RAM in the computer than is really there.
Multitasking
- Multitasking refers to the running of multiple independent computer programs on the same computer; giving the appearance that it is performing the tasks at the same time.
- An operating system kernel contains a scheduling program which determines how much time each process spends executing, and in which order execution control should be passed to programs. Control is passed to a process by the kernel, which allows the program access to the CPU and memory. Later, control is returned to the kernel through some mechanism, so that another program may be allowed to use the CPU. This so-called passing of control between the kernel and applications is called a context switch.
Disk access and file systems
- File systems allow users and programs to organize and sort files on a computer, often through the use of directories (or "folders").
- Access to data stored on disks is a central feature of all operating systems.
- Computers store data on disks using files, which are structured in specific ways in order to allow for faster access, higher reliability, and to make better use out of the drive's available space.
- The specific way in which files are stored on a disk is called a file system, and enables files to have names and attributes. It also allows them to be stored in a hierarchy of directories or folders arranged in a directory tree.
Device drivers
- A device driver is a specific type of computer software developed to allow interaction with hardware devices.
- It constitutes an interface for communicating with the device, through the specific computer bus or communications subsystem that the hardware is connected to, providing commands to and/or receiving data from the device, and on the other end, the requisite interfaces to the operating system and software applications.
- It is a specialized hardware-dependent computer program which is also operating system specific that enables another program, typically an operating system or applications software package or computer program running under the operating system kernel, to interact transparently with a hardware device, and usually provides the requisite interrupt handling necessary for any necessary asynchronous time-dependent hardware interfacing needs.
- The key design goal of device drivers is abstraction.
2. NETWORKING
- Currently most operating systems support a variety of networking protocols, hardware, and applications for using them.
- This means that computers running dissimilar operating systems can participate in a common network for sharing resources such as computing, files, printers, and scanners using either wired or wireless connections.
- Networks can essentially allow a computer's operating system to access the resources of a remote computer to support the same functions as it could if those resources were connected directly to the local computer.
- This includes everything from simple communication, to using networked file systems or even sharing another computer's graphics or sound hardware. Some network services allow the resources of a computer to be accessed transparently, such as SSH which allows networked users direct access to a computer's command line interface.
- Client/server networking allows a program on a computer, called a client, to connect via a network to another computer, called a server. Servers offer (or host) various services to other network computers and users. These services are usually provided through ports or numbered access points beyond the server's network address. Each port number is usually associated with a maximum of one running program, which is responsible for handling requests to that port. A daemon, being a user program, can in turn access the local hardware resources of that computer by passing requests to the operating system kernel.
- Many operating systems support one or more vendor-specific or open networking protocols as well, for example, SNA on IBM systems, DECnet on systems from Digital Equipment Corporation, and Microsoft-specific protocols (SMB) on Windows.
- Specific protocols for specific tasks may also be supported such as NFS for file access. Protocols like ESound, or esd can be easily extended over the network to provide sound from local applications, on a remote system's sound hardware.
3. SECURITY
- A computer being secure depends on a number of technologies working properly. A modern operating system provides access to a number of resources, which are available to software running on the system, and to external devices like networks via the kernel.
- The operating system must be capable of distinguishing between requests which should be allowed to be processed, and others which should not be processed. While some systems may simply distinguish between "privileged" and "non-privileged", systems commonly have a form of requester identity, such as a user name. To establish identity there may be a process of authentication.
- Often a username must be quoted, and each username may have a password.
- Other methods of authentication, such as magnetic cards or biometric data, might be used instead.
- In some cases, especially connections from the network, resources may be accessed with no authentication at all (such as reading files over a network share).
- Internal security, or security from an already running program is only possible if all possibly harmful requests must be carried out through interrupts to the operating system kernel. If programs can directly access hardware and resources, they cannot be secured.
- External security involves a request from outside the computer, such as a login at a connected console or some kind of network connection. External requests are often passed through device drivers to the operating system's kernel, where they can be passed onto applications, or carried out directly. Security of operating systems has long been a concern because of highly sensitive data held on computers, both of a commercial and military nature.
- The United States Government Department of Defense (DoD) created the Trusted Computer System Evaluation Criteria (TCSEC) which is a standard that sets basic requirements for assessing the effectiveness of security.
4. USER INTERFACE
- The user interface is usually referred to as a shell and is essential if human interaction is to be supported.Every computer that is to be operated by an individual requires a user interface.
- The user interface views the directory structure and requests services from the operating system that will acquire data from input hardware devices, such as a keyboard, mouse or credit card reader, and requests operating system services to display prompts, status messages and such on output hardware devices, such as a video monitor or printer.
- TYPES- GUI ( Graphical User Interface) , Command line interfaces , Touch screens , Hardware Interfaces etc.
FUNCTIONS OF OPERATING SYSTEM
1. BOOTING THE COMPUTER
- In computing, booting (or booting up) is the initialization of a computerized system. The system can be a computer or a computer appliance.
- The booting process can be "hard", after electrical power to the CPU is switched from off to on (in order to diagnose particular hardware errors), or "soft", when those power-on self-tests (POST) can be avoided.
- Soft booting can be initiated by hardware such as a button press, or by software command.
- Booting is complete when the normal, operative, runtime environment is attained.
- A boot loader is a computer program that loads an operating system or some other system software for the computer after completion of the power-on self-tests; it is the loader for the operating system itself, which has its own loader for loading ordinary user programs and libraries.
2. PROVIDES USER INTERFACE
- In information technology, the user interface(UI) is everything designed into an information device with which a human being may interact -- including display screen, keyboard, mouse, light pen, the appearance of a desktop, illuminated characters, help messages, and how an application program or a Web site invites .
- The operating system is responsible for providing a consistent application program interface (API) which is important as it allows a software developer to write an application on one computer and know that it will run on another computer of the same type even if the amount of memory or amount of storage is different on the two machines.
3. PERFORMS BASIC COMPUTER TASK
- Managing peripheral devices like mouse , keyboard.
- Most operating systems now are plug and play which means a device such as a printer will automatically be detected and configured without any user intervention.